What are ACLs? Link to heading
ACL (Access Control List) is a technology that allows administrators to control access to the network by filtering packets based on source/destination IP, layer 4 ports, etc. This is set on the interface either inbound or outbound. The list is processed from top to bottom. So if you have a list that goes 2,3,1, the order of processing would be 2 then 3 then 1.
Types of ACL Link to heading
There are two types: extended and standard. The difference is that standard ACLs are only based on source IP address, but extended ACLs are based on source/destination IP addresses or port numbers. Standard ACLs can only use numbers 1-99 or 1300-1999.
Basic Commands Link to heading
I am going to show you the command on a Cisco router that lets you see information about ACLs. The main command to show you the list is:
do sh access-lists
Configure access control Link to heading
This is the topology of the network we are going to use:
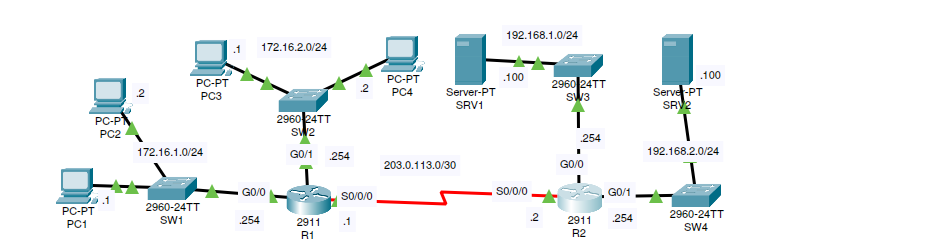
We are going to configure R2
ip access-list standard TO_192.168.1.0/24
This will create a standard list named TO_192.168.1.0/24.
- Then we want to configure this list with:
permit 172.16.1.0 0.0.0.255
permit 172.16.2.0 0.0.0.255
deny any
The permit command is the rule to allow traffic from the source IP address, then 0.0.0.255 is the wildcard mask. To find this, take your subnet mask and subtract 255 from each octet and this will give you your wildcard mask.
- Then we want to apply this to a interface:
interface g0/0
ip access-group TO_192.168.1.0/24 out
So “int g0/0” is just going into the interface, then “ip access-group” is the command to apply an ACL to an interface. TO_192.168.1.0/24 is the list name. Finally, “out” specifies how to interact with the rule. You can use “out” or “in”. “Out” means that the rule will be applied to packets exiting the interface, and “in” is when a packet is entering the interface.
- Verfy the rule. The reason you do this is because ACL are really dangrous. You can lock yourself out from remoting in and block user from access resource on the network or the internet.
do sh access-lists
Conclusion Link to heading
This covers standard ACLs. I will do a post on how to do extended lists another day. This should give you enough information to learn standard ACLs, but please test it in a lab environment before implementing on a production network.